Have you ever had an executive tell you to just “put it in the cloud?” It’s a deceptively simple command, and an increasingly common one, too. No one wants to break the news to their boss that the task isn’t as easy or inexpensive as it seems,
especially when you’re dealing with sensitive data. That’s because it requires planning, strategy, and expert implementation to successfully place that data into a cloud ecosystem.
What is Sensitive Data?
The definition may vary from company to company, but sensitive data is generally considered any information that makes up the most important components of mission-critical business systems. When storing these files, it’s important to consider the following tenets of data security and governance:
- Data availability
- Confidentiality
- Integrity
- Regulatory and compliance considerations
- Performance and cost issues
In other words, sensitive data must be quickly and efficiently accessed without interruption, but it cannot be breached or hard to control.
How Can Organizations Strategically Protect Sensitive Data?

The leading cloud strategies of today are the result of years of evolution within the industry. Cloud solutions are more agile, secure, and accessible than ever before, and they’re multiplying at a torrid rate, with enterprises across all industries using an average of 1,181 separate cloud services.1 That’s an alarmingly high number that raises several security concerns around the sharing of sensitive data. However, with a more careful approach to your strategy, you can avoid the overuse of cloud services.
Planning Considerations
- Think of your journey to the cloud as incremental steps, not an all-or-nothing proposition—especially when it comes to mission-critical applications.
- Consider a hybrid environment that offers a combination of public cloud services and a hosted IT infrastructure. This will allow for more private handling of mission-critical workloads and sensitive data that require PCI or HIPAA compliance.
- If your data contains sensitive financial or government information, ensure that your cloud solutions offer strict controls to help you comply with country-specific requirements, such as GDPR regulations.
- Make note of any legacy applications that may require traditional bare-metal solutions and isolation from other customers.
Isolating Sensitive Data With a DMZ
In cases where sensitive data is maintained in a public cloud, a multi-tier network architecture is deployed. This strategy creates a so-called “demilitarized zone,” or DMZ, that isolates sensitive data 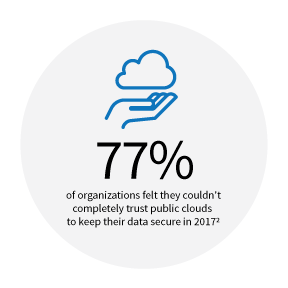 from public-facing web servers. Alternatively, customers may opt to utilize a “zero-trust” architecture to secure their sensitive data from both external and internal threats. In this scenario, those who try to access data throughout the network are asked to verify their identity and permissions each time they want access, when they change locations, or after they attempt to breach pre-determined parameters. This type of architecture becomes even more attractive in a hybrid solution where full control of all endpoints is not possible or preferable.
from public-facing web servers. Alternatively, customers may opt to utilize a “zero-trust” architecture to secure their sensitive data from both external and internal threats. In this scenario, those who try to access data throughout the network are asked to verify their identity and permissions each time they want access, when they change locations, or after they attempt to breach pre-determined parameters. This type of architecture becomes even more attractive in a hybrid solution where full control of all endpoints is not possible or preferable.
Currently, we’re seeing very few companies store sensitive data solely in the cloud. In fact, only 23% of organizations felt they could completely trust public clouds to keep their data secure in 2017.2 Companies in their infancy might give pure cloud deployments a try, but the reality is that as their business grows, cost, complexity, and security concerns come into play. Wide-scale data breaches have also left customers wary of cloud-based storage, and many brand reputations have been damaged in the wake of these incidents. While these issues are most often due to misconfigurations, they sometimes can be traced to the rapid and uncontrolled sprawl of cloud services, a weak integration strategy, and a failure to adopt a true hybrid cloud architecture that isolates sensitive data while enabling elasticity.
The Case for Hybrid Cloud Services

To keep sensitive data safe from breaches, many enterprises are opting to keep it on dedicated, bare-metal infrastructures. With hybrid cloud services, such as Direct Connect capabilities through their hosting and MSP partners, they can bridge to the public cloud at the same time. This allows organizations to set up virtual private clouds that can securely transmit data between an on-premises or dedicated hosted infrastructure to their public cloud resources.
Hybrid cloud adoption increased three-fold between 2016 and 2017,2 likely due to the fact that this strategy allows organizations to:
- Pay for infrastructure on a monthly basis
- Enjoy the performance and control of bare-metal infrastructures
- Avoid large Capex outlays
- Physically secure their infrastructure
A Promising New Chapter for Sensitive Data
It should go without saying that no two organizations’ needs are the same, especially when it comes to storing sensitive data. But one thing is clear—a rush job isn’t going to cut it. Instead, select a technology partner that offers a custom and targeted approach. Together, you can carefully plan and develop a solution that’s secure, affordable, and customized to meet the needs of your organization.
See the Hybrid Cloud in Action
Ntirety’s global enterprise customers trust our expertise to manage their infrastructure containing their most sensitive data. When Samsung needed to secure their SmartTV application, it was Ntirety that enabled them to be the first smart television app to be PCI compliant globally. Ntirety has the in-depth expertise to design, build, secure, and operate infrastructures containing highly-sensitive, mission-critical data, including PCI-, FERPA-, and HIPAA-compliant infrastructures.
Talk to one of our Security Experts, or get a free Security Assessment »
- Netskope, February 2018.
- McAfee, 2017. Building Trust in a Cloudy Sky: The state of cloud adoption and security.