From the moment any data system comes online, it is at risk of breach. Modern workloads and data reside, change, and grow in a medium of capabilities and simultaneous risk. In the wild, more than a million cyberattacks occur on the web on average each day. The odds of avoiding becoming a target are simply not very good. The need for continual cybersecurity measures is extremely prevalent, and there is a call for programs that feature heightened vigilance and performance in the face of modern threats.
Threats to Financial Teams
Financial teams are in an especially exposed position. Their data is a high-value target treading in a mass of computing largesse, and any leak could pose an existential threat to their careers, not to mention the company itself. The implications of just one successful attack could cost millions, and thus CFOs have grown to be shared custodians of cybersecurity initiatives. CFO executives have started to focus on cybersecurity solutions with more emphasis than ever before, and to explore the depths of current cybersecurity threat conditions. What this exploration has revealed is that the familiar benefits of frameworks can be applied towards solutions.
The Familiarity of Frameworks
Framework systems build on basic concepts and controls, and work as scaffolding systems that guide efforts through reporting, analysis, and workflows. Financial professionals are familiar with frameworks, as the framework is the core of financial operations. Without it, a business would lose control over finances and ultimately fail to succeed.
Over the years, as threat and risk conditions have escalated, the setting for advanced cybersecurity measures has moved out of the server room (and the hands of information technology teams) and to the executive table. Championed by the CFO and other executives, this change demands direct access to the board and the budget planning process. Cybersecurity investments are critical and significant, and along with those characterizations the familiar standards of frameworks have proven to provide valuable measurement of risks, controls, and performance.
The NIST Standard
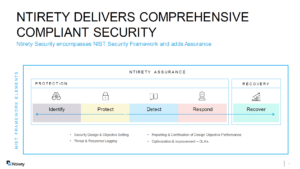
One of the most accepted cybersecurity frameworks is the NIST standard known as the “NIST Cybersecurity Framework.” The NIST Cybersecurity Framework covers five key functions:
- Identify
- Protect
- Detect
- Respond
- Recover
Organizations are leveraging this framework as an anchor to build an approach that is repeatable, flexible, prioritized, cost-effective, and based on performance. In other words, the NIST framework checks all the boxes as it offers guidance and assistance toward the management of cybersecurity risks. Prevention, ruling measures, and the ability to recover in the event of an attack are all rolled into the framework.
The NIST framework has gained merit with C-suites, boards, and CFOs, and it’s important to recognize its value in the cybersecurity conversation – and in providing a high-level overview of the business and its protections. Digging deeper, specific NIST publications (SP 800-171 and SP 800-53, as examples) offer more than 100 controls and measures and provide a roadmap to a better secured, lower risk future. These serve as the vehicle of justification for cybersecurity initiatives, creating greater success in the mission and for the business.
Cybersecurity as Business Imperative
Once relegated to information technology teams, cybersecurity has taken on an appropriate scope of enterprise-wide focus. Financial executives have stepped up to the risks and challenges of an age where traditional security mindsets cannot meet the standards of acceptance. Due to its existential nature and massive financial implications, cybersecurity has become the most significant risk to the business. Security frameworks have created a consumable channel at the executive table, providing valuable guidance towards better security practices and technologies.
With any framework in place, the business begins to gain insight into and confidence in its measures. This applies in both financial matters and cybersecurity. With cybersecurity frameworks, organizations can leverage the virtual blueprints that emerge to create effective actions that feed directly into their cybersecurity infrastructure. These frameworks can take their place in technology decisions, as planning plus action equals results and improvements. Cybersecurity frameworks such as NIST help organizations assess and build actionable plans and determine exposure to risks.
Cybersecurity guidance that is derived from a framework approach offers the most value when tactical points are matched up to actions. Organizations can pragmatically build out on a custom cyber-resilience strategy that aligns with the extremely individual context of an organization’s assumption of risks.
How Ntirety Can Help
Ntirety Compliance Services provide a comprehensive and reliable solution for ensuring your business remains compliant with industry regulations and NIST standards. Our team of experienced compliance experts will work closely with you to assess your current compliance posture, identify any potential gaps, and develop a customized plan to help your organization achieve and maintain compliance. With Ntirety services, you can feel confident your business is meeting all the necessary requirements and avoid costly penalties or other negative consequences. By choosing Ntirety Compliance Services, you can focus on running your business while we take care of the complicated compliance issues.