C-Levels, and specifically CFOs and other financial executives, have increasingly used NIST standards to respond to cybersecurity requirements and the significant data risks they address. This transition of framework practices is possible in large part due to the existence of similar controls and measures in traditional finance operations.
The NIST framework helps organizations define full-cycle solutions for assisting in planning and management, measurement and analysis, and response systems. The systems can provide answers and refinement to issues such as:
- Defining asset protection in strategy and planning
- Plans to meet the requirements of critical infrastructure operations
- Evaluation of incident response capabilities
- Evaluation of incident communication plans
- Identification of critical assets, along with risks and vulnerabilities
- Plans to meet the standards of regulatory requirements
The list expands from there and, as described in the previous article, an organization can use the NIST framework to quickly build a roadmap to better security. Perhaps the biggest takeaway is that effective cybersecurity programs are proactive and continuous, aligning with operational strategies throughout. Additionally, frameworks can serve as a specific backbone towards maintenance and improvement.
NIST Highlights
Let’s dig into the tenants of the NIST Cybersecurity Framework, which is composed of the following five elements:
- Identify: Identify the cybersecurity risk (vulnerabilities) to systems, people, assets, data, and capabilities
- Protect: Safeguard to ensure delivery of critical services
- Detect: Identify the occurrence of a cybersecurity event
- Respond: Take action regarding a detected cybersecurity incident
- Recover: Support timely recovery to normal operations to reduce the impact from a cybersecurity incident
The framework helps companies create measures for practical cyber-incident prevention, response, and overall security design.
Ntirety: Beyond NIST
At some point, cybersecurity framework outcomes need to align with efforts. Cybersecurity is unique because of the systems and requirements involved; when cybersecurity is applied in a company environment, it is always layered through activities that build towards a complete solution. Complete is what we should all strive for, where nothing is left unmonitored, unverified, or unanswered.
Ntirety answers the total solution by leveraging its approach to NIST outcomes. Ntirety groups the five elements outlined above into two broad categories: Protection and Recovery. It wraps the elements within an Assurance service designed to ensure the enterprise meets any outside requirements and the standards it has set for itself.
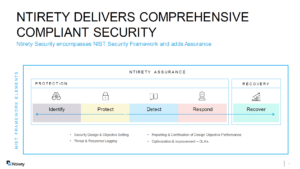
Figure 1: Ntirety Cybersecurity Framework Grouping – Comprehensive Compliant Security
Finance leaders will recognize the following categories, which are contextually analogous to NIST frameworks. First, we can regroup the NIST framework elements by dividing them into the two primary categories that define Internal Control frameworks, which are:
Preventive
- Identify: Finding the vulnerabilities
- Protect: Implementing the systems and applications to close the identified vulnerabilities
Detective or Mitigating
- Detect: Identify the occurrence of cybersecurity events
- Respond: Take action against the CS event
- Recover: Timely return to normal operations, minimizing the impact of the cybersecurity incident
Most Competitors are Single Track
By comparison, every competitor falls into an approach that offers these general services:
Protection Focus
- Assessment Firms: Primarily do project-based work to identify cybersecurity vulnerabilities
- Protection Technology Firms: Often hardware or application vendors (i.e. firewall firms, endpoint protection technology companies)
Detection/Mitigation Focus
- Managed Detection & Response (MDR) Service/Technology Providers
- Firms that specialize in mitigating cybersecurity incidents by identifying and addressing the cybersecurity event. These firms are mix of technology providers to facilitate MDR and service providers
DRAAS & Backup Service Providers
- A mix of application and service providers, providing technologies or the DR or backup service. These are often not focused on security, but only in providing recovery from a platform or application failure
COMPREHENSIVE Compliant Security is Different
Unlike the competition, Ntirety’s comprehensive security solutions encompass both Protection and Mitigation in the context of financial controls. Further, unlike MDR firms Ntirety provides Secure Disaster Recovery as a Service (DRaaS) and Backup services. The competition generally addresses only a portion of the five elements of the NIST Cybersecurity Framework, leaving the enterprise to manage the interoperation of various services, technologies, and applications – and often to execute the response actions provided by their MDR service providers.
Ntirety: NIST Foundation and Financial Sanctity
Corporate governance, auditing, and frameworks allow executives, employees, and shareholders to keep financials in line with expectations. In cybersecurity, similar measures help guide a countless number of companies on their journey to improved operations and capability to respond and recover from cybersecurity incidents. Ntirety has built an industry-unique Comprehensive Compliance Security system that covers the complete NIST framework, adding Assurance to its features. With comprehensive Ntirety services, clients excel on their cybersecurity initiatives and benefit from more than 25 years of experience in designing, building, operating, and securing client environments.